DeFi platform Unizen has committed to providing immediate reimbursements to users affected by a recent exploit that resulted in a loss of approximately $2.1 million in user funds.
After blockchain analytics firm PeckShield identified an “approve issue” on March 9, reporting a drain of over $2 million from the DeFi platform, users were advised to revoke approvals from the trade aggregator to prevent further losses.
Hi @unizen_io you may want to a look. It looks like an approve issue with >2m loss already.
If you have approved the following trade aggregator, please revoke ASAP:
eth: 0xd3f64baa732061f8b3626ee44bab354f854877ac pic.twitter.com/Rq1AMxrrgs
— PeckShield Inc. (@peckshield) March 8, 2024
Security company SlowMist estimated the exploit losses at around $2.1 million, with the attacker swapping Tether USDT for the stablecoin DAI.
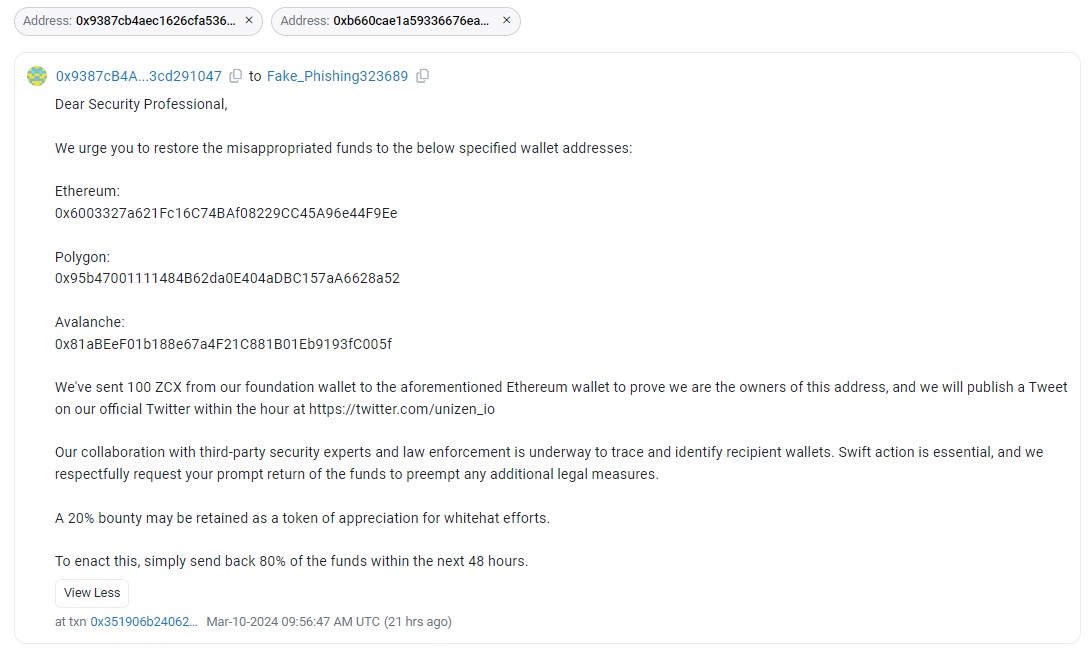
In response, Unizen initiated negotiations with the hacker, offering a 20% bounty for the return of the remaining stolen funds and began collaborating with law enforcement and forensic experts to identify the attacker.
While bounty negotiations continue, Unizen swiftly moved to reimburse victims of the hack. The company announced plans to refund 99% of affected users, with refunds starting on March 11.
Dear unizen community,
After an arduous weekend, we have made the strategic decision to make over 99% of those affected from our community completely whole with immediate effect.
Our CEO / Founder, Sean Noga, has decided to loan Unizen the majority of the immediate… pic.twitter.com/d9GyaH3j8Y
— unizen (@unizen_io) March 11, 2024
Founder and CEO Sean Noga personally provided funds to facilitate the reimbursements, focusing on users who lost less than $750,000.
Reimbursements will be made in USDT or USDC, with larger losses handled on a case-by-case basis. Alongside the reimbursement announcement, Unizen shared a video guide to help users review and revoke approvals within the platform to mitigate further losses.
Unizen’s Chief Technology Officer, Martin Granström, confirmed that they have gathered sufficient evidence for a post-mortem report and are collaborating with third-party firms on the investigation. The company intends to release an incident report soon and has pledged to enhance security measures moving forward.
Quick update.
We've collected a ton of evidence and have enough to proceed with the post-mortem. We're working with third party security firms and law enforcement to track down the identity of the hacker.
On Monday we will have a draft of the post-mortem ready for the…
— Martin Granström (@MartinGranstrom) March 10, 2024












